So much of the Internet of Things is still in the gee-whiz stage that we haven’t seen much in terms of nuanced IoT strategies. By that I mean ones that carefully weigh tradeoffs between companies and consumers to try to find strategies that are mutually beneficial and recognize there are new factors at play in IoT strategies, such as privacy and data mining, that may have positive or negative consequences for the customer/company interplay.
Deloitte’s “University” has made an important step in that direction with its “Power Struggle: Customers, companies and the Internet of Things” paper, co-authored by Brenna Sniderman and Michael E. Raynor.
In it, they explore how to create sustainable strategies that will be mutually beneficial to the customer and company — which are not always immediately apparent, especially when you explore the subtleties of how these strategies might play out in the new reality of the Internet of Things.
The study’s goal was to understand the factors that can distort IoT’s benefits, and instead create win-win IoT strategies.
Sniderman and Raynor suggest there are four quadrants into which a given strategy might fall:
- (the sweet spot!) “All’s well: Sufficient value is created, and that value is shared between customers and companies sufficiently equitably such that both parties are better off and feel fairly treated.
- “Hobson’s choice: A Hobson’s choice exists when you’re free to decide but only one option exists; thus, it is really no choice at all…. Even when customers come out ahead compared with their former options, their implied powerlessness can lead to feelings of unfairness.
- “Gridlock: In their quest for value capture, both sides are pulled in opposite directions, with neither able to move toward an optimal outcome. Here, both parties recognize IoT enablement as something that should lead to success, but neither party is able to reach it, since their competing interests or different value drivers are working at cross purposes.
- “Customer is king: Although particular IoT deployments might make economic sense for companies, customers end up capturing a disproportionate share of the new value created, pulling this outcome more in the customers’ favor; Craigslist is an obvious example.”
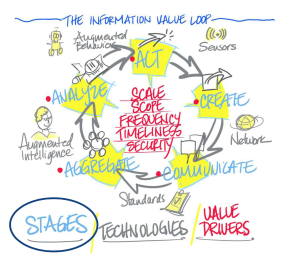
According to the authors, a key to finding the win-win, “all’s well” solution is the Information Value Loop (which I first discussed last Spring) that creates value out of the vast increase in information made possible by the IoT.
As I mentioned then, “This fits nicely with one of my IoT ‘Essential Truths,’ that we need to turn linear information flows into cyclical ones to fully capitalize on the IoT.” When you do that, it’s possible to design continuous improvement processes that feed back data from actual users to fine tune products and processes. GE has found it leads to much shorter iterative loops to design improved versions of its products.
Here’s the gussied-up version of the cool hand-drawn visualization from the Deloitte brainstorming session that led to the Information Value Loop (print it & place it on your wall next to the one on privacy and security that I wrote about a while ago):

Deloitte Information Value Loop
The information no longer flows in linear fashion: it’s created from using sensors to record how things act in the real world, then goes through the various stages of the loop, each of which is made possible by one of the new technologies enabling the IoT. The goal is either enhanced M2M integration among things, or improved actions by humans, and, to be sustainable over time:
“A value loop is sustainable when both parties capture sufficient value, in ways that respect important non-financial sensibilities. For example, retailer-specific and independent shopping apps can use past browsing and purchasing history—along with other behaviors—to suggest targeted products to particular customers, rather than showing everyone the same generic products, as on a store shelf. Customers get what they want, and companies sell more.
… “The amount of value created by information passing through the loop is a function of the value drivers identified in the middle. Falling into three generic categories—magnitude, risk, and time—the specific drivers listed are not exhaustive but only illustrative. Different applications will benefit from an emphasis on different drivers.”
OK, so how does this theory play out?
Sniderman and Raynor picked a range of IoT-informed strategies to illustrate the concept, some of which may include unintended consequences that would harm/turn off customers or companies. For example, “An ill-considered push for competitive advantage could well overreach and drive away skittish customers. Alternatively, building too dominant an advantage may leave customers feeling exploited or coerced, a position unlikely to prove viable in the long term.”
Understanding the underlying structure of each type of loop is critical, because they naturally pull an IoT strategy in a particular, divergent way.
The example they pick to illustrate the “all’s well” quadrant of results is the dramatic increase in built-in diagnostic technology in cars. This is of great personal interest: genetic testing has revealed that I am one of the approximately 10% of men who are missing the male car gene: I can’t stand the things, and view them as a big block of metal and plastic just waiting to develop problems (or, ahem, get hit by deer …), so I need all the help I can get. Sniderman and Raynor zero in on maintenance as one area for win-win benefits for drivers and dealers through the IoT:
“Customers often have little understanding of which repairs are necessary, feel inconvenienced by having to go without their car during maintenance periods, and are frustrated by potential overcharges. In response, automakers are embedding sensors that can run a wide range of reliable diagnostics, allowing a car to “self-identify” service issues, rather than relying on customers (“Where’s that squeaking coming from?”) or mechanics (“You might want to replace those brake pads, since I’ve already got the wheels off”). This creates a level of objectivity of obvious customer value and enables automakers to differentiate their products. Interactive features that work with customers’ information can further add value by, for example, potentially syncing with an owner’s calendar to schedule a dealership appointment at a convenient time and reserving a loaner vehicle for the customer, pre-programmed with his preferences to minimize the frustration of driving an unfamiliar car.
In this scenario, both parties collaborate to provide and act on data, in a mutual exchange of value. The customer captures value in multiple ways: He enjoys increased convenience and decreased frustration, improved vehicle performance and longer operating life, reduced maintenance charges, and—since almost everything about this interaction is automated—fewer occasions for perceived exploitation at the hands of unscrupulous service providers.
Value capture extends to companies in the form of ongoing customer interaction. Linking maintenance programming to the dealership encourages customers to return for tune-ups rather than go elsewhere, ideally leading to continued purchases in the long term. OEMs can also access data regarding vehicle maintenance issues and may be able to identify systematic malfunctions worthy of greater attention. Dealers also have an opportunity to make inroads into an untapped market: Currently, just 30 percent of drivers use the dealer for routine maintenance…”
Kumbaya! But then there’s the opposite extreme, according to Sniderman and Raynor, represented by smart home devices, which would lead to the lose-lose, gridlock scenario. I think they seriously underestimate the understanding already by manufacturers in the field that they need to embrace open standards in order to avoid a range of competing standards (Zigbee, Bluetooth, etc.) that will force consumers to invest in a variety of proprietary, incompatible hubs, and therefore discourage them from buying anything at all. All you have to do is look at new hubs, such as Amazon’s Echo, which can control devices from WeMo, Hue, Quirky, Wink — you name ’em, to realize that sharing data is already the norm with smart home devices.
Because this missive is getting long, I’ll leave it to you, dear reader, to investigate Sniderman & Raynor’s examples of the “customer is king” scenario, in which the customer grabs too much of the benefit (have to admit, a lot of the location-based IoT retail incentives still give me the creeps: I hate shopping under the best of circumstances, and having something pop up on my phone offering me an incentive based on my past purchases makes a bad experience even worse. How about you?); and the “Hobson’s choice” one, in which usage-based car insurance runs amok and insurers begin to charge unsafe drivers a surcharge — as documented by the devices such as Progressive’s “Snapshot” (I was dismayed to read in the article that Progressive is in fact doing that in Missouri, although I guess it’s a logical consequence of having objective evidence that someone consistently drives unsafely).
I can’t help thinking that the 800-pound gorilla in the room in many of these situations are the Scylla and Charybdis of the IoT, threats to privacy and security, and that makes it even more important that your IoT strategies are well thought out.
They conclude that, from my perspective, data isn’t just enough, you also need the decidedly non-technical tools of judgment and wisdom (aided by tools such as their Information Value Loop) to come up with a sustainable, mutually advantageous IoT strategy:
“Identifying where the bottlenecks lie (using the Information Value Loop), how each party is motivated to respond, and seeking to shape both incentives and the value loop itself puts companies more in control of their destinies.
“Second, taking a hard look at who benefits most from each IoT-enabled transaction, understanding when a lopsided value-capture outcome tips too far and becomes unsustainable, and taking steps to correct it may also lead to long-term success.
“Lastly, an honest assessment of where IoT investments may not have an appreciable benefit—or may decrease one’s potential for value capture—is just as crucial to a company’s IoT strategy as knowing the right places to invest.”
I may quibble with some of their findings, such as those about smart homes, but bravo to Sniderman and Raynor for beginning what I hope is a spirited and sustained dialogue about how to create sustainable, mutually-advantageous IoT strategies! I’ve weighed in with my Essential Truths, but what are you thinking about this critical issue, often overlooked in our concentration on IoT technologies?